Yet Another Awesome Undocumented Hidden Feature in the new Cisco Firepower 6.4 code!
Okay, so in my last couple blogs I mentioned some undocumented or hidden “features” in the new code.
Here is a reminder of the two I already mentioned:
- If you blacklist an IP address, the address is immediately blacklisted and all communication stops. However, in the past, if you wanted to remove the IP address from the blacklist you had to redeploy to make this take effect. Starting in 6.3 code this is no longer true as there is a silent push of the change to the FTD devices….this is a huge change and very well needed! Crickets from Cisco on this…but thank you, we’ll take it.
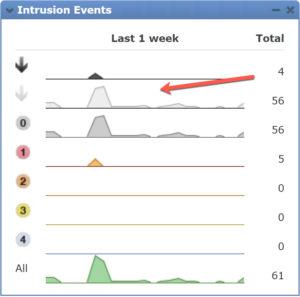
2. If you wanted to see a graph of the IPS events and see a time range of the “would have dropped packets”, you need to go to Dashboards>Intrusion Events>Add Widgets and then choose the Intrusion Events graph again. The new graph found in the widget categories provides the “would have dropped” category where the default table does not.
If you like graphs, this is really, really helpful if you are fine tuning your IPS policy, and you can use the Report Designer to create a report template from this graph!
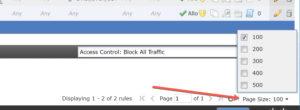
3. Also in 6.4 there is a hidden gem at the bottom of your ACP rules:
Notice you can now choose up to 500 rules to see on a single page instead of just the default of 100! For some of my customers this will be awesome!
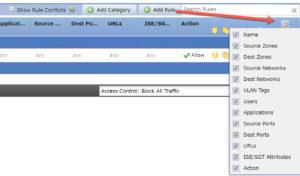
4. Finally, there is an awesome yet undocumented new features on the top of the ACP rules page. Click the gear in the upper right hand corner above your first rule:
You can now choose the categories you want to see! Wish they had this feature on the Connection Events page too.
Also, crickets from Cisco on this too; I just happened to see it today!
Cheers!

I just noticed that Rules per Page option after upgrading to FMC 6.3.0.3, so it seems Cisco had a change of heart and one doesn’t need to upgrade to a not yet ready 6.4.0(1) to get that option.
oh wow, I went and looked at my 6.3.0.1 FMC and didn’t’ see it. That’s awesome that they added this in 6.3.0.3, which is a very stable code!
Why do some customers need over 100 ACL rules? Are they trying to reduce logging ? Or having to create specific pin pointed bypass rules over and over?
Hi Evan, I have customers with over 10,000 ACP rules! Yes, its true, and a lot of my customers have 3000 or 4000! They need granular control over applications, and rules can grow quickly in a large enterprise.