A new FTD device is not like the new ASA was….
There are differences between a brand new shiny powerful FTD box and what we’re use to with the ASA’s we’ve been installing since 2005.
When you installed an ASA there were some default configs that provided security out of the box; just add your IP’s and security levels on your interfaces and you actually had some simple security. For example, the global policy inspected some default protocols and the security levels set our interface access…pretty nice…and for good measure, ICMP was not inspected on the interfaces, which added an additional security level.
With FTD, none of this is configured, which means ICMP is wide open.
To simply stop this, at a minimum, you need to set the ICMP Platform setting to disable ICMP type 8 on the Outside zone. Here is how you do that:
1. Go to Devices>Platform Settings and then click on ICMP
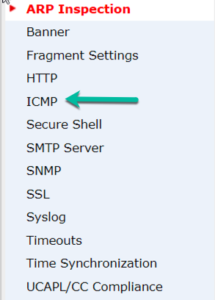
2. On the ICMP page, choose Add to create the first ICMP rule. If your zones are not available at this point, you need to stop and configure them.
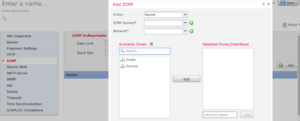
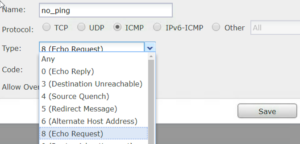
3. You must set the Deny rule first. Go to Objects>Ports or choose the Green + to create the objects on this page – either way. On the Object port create page, choose ICMP and Type 8, which will stop Echo, then press Save.
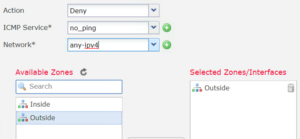
4. Now, add the newly created ICMP object into the rule along with the deny, any-ipv4, Outside zone and then press Save.
5. You cannot just have a Deny rule in this policy – it’s like an ACL, so you must permit something. On the ICMP main page, click Add and create a Permit rule with a new object that allows all ICMP. Pretty simple, just choose ICMP and then Save.
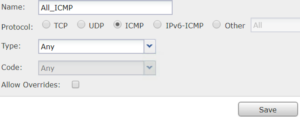
6. In the new rule add Permit, your new object, any-ipv4 and Outside zone and then Save. Your ICMP policy should look something like this:
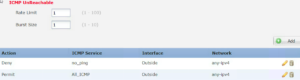
Before you deploy, test that you can ping the Outside interface. Then deploy and test again – now you shouldn’t be able to ping the interface.

Hi Todd, I am just trying to allow pings to my FTD box(2120) from the outside, from some particular IPs
I have created a policy allowing this but the pings keep failing
So you can ping the interfaces of FTD by default, but not route pings through by default
When you say you created a policy to allow this, what exactly does that mean? If you mean an ACP rule, I’d like to see it
Thanks, Todd Lammle
Hi Todd, great info you have here because is very difficult found things about Firepower management and i don’t feel comfortable with those equipments.
You know that i am able to ping to my GW but i cannot ping anywhere from the Firepower to any destination. Example:
> show arp | include Some-Network
Some-Network 10.216.116.49
Some-Network 10.216.116.50
Some-Network 10.216.116.56
Some-Network 10.216.116.57
Some-Network 10.216.116.48
Some-Network 10.216.116.58
Some-Network 10.216.116.53
Some-Network 10.216.116.54
Some-Network 10.216.116.47
Some-Network 10.216.116.60
Some-Network 10.216.116.55
Some-Network 10.216.116.59
Some-Network 10.216.116.52
Some-Network 10.216.116.46
> ping 10.216.116.46
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.216.116.46, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
Do you have any clue for this behavior?
Yes, sure, you need to tell it what interface.
Try this:
>ping system 1.1.1.1
that tells it to use the management interface and should work for you.
Todd
First to all kindly thanks for reply to my request. Yes in one of the test i also put the interface Name and did’t work. The firewalls are working properly, but one of the things that i don’t understand is the exit of the command “show interface ip brief” show the next:
> show interface ip brief
Interface IP-Address OK? Method Status Protocol
Internal-Data0/1 unassigned YES unset up up
Port-channel48 5.5.5.1 YES unset up up
Internal-Data1/1 169.254.1.1 YES unset up up
Management1/1 unassigned YES unset up up
Ethernet2/1 unassigned YES unset admin down down
Ethernet2/2 unassigned YES unset admin down down
Ethernet2/3 unassigned YES unset admin down down
Ethernet2/4 unassigned YES unset up up
Ethernet2/4.113 unassigned YES CONFIG up up
Ethernet2/4.200 unassigned YES CONFIG up up
Ethernet2/4.300 unassigned YES CONFIG up up
Ethernet2/4.301 unassigned YES CONFIG up up
Ethernet2/4.303 unassigned YES CONFIG up up
Ethernet2/4.400 unassigned YES CONFIG up up
Ethernet2/4.402 unassigned YES CONFIG up up
Ethernet2/4.500 unassigned YES CONFIG up up
Ethernet2/4.501 unassigned YES unset up up
Ethernet2/4.502 unassigned YES CONFIG up up
Ethernet2/4.503 unassigned YES CONFIG up up
Ethernet2/4.504 unassigned YES CONFIG up up
Ethernet2/4.505 unassigned YES CONFIG up up
Ethernet2/4.506 unassigned YES manual up up
Ethernet2/4.507 unassigned YES manual up up
Ethernet2/4.509 unassigned YES manual up up
Ethernet2/4.510 unassigned YES manual up up
Ethernet2/4.511 unassigned YES manual up up
Ethernet2/4.550 unassigned YES CONFIG up up
Ethernet2/4.600 unassigned YES CONFIG up up
Ethernet2/4.700 unassigned YES CONFIG up up
Ethernet2/4.701 unassigned YES CONFIG up up
Ethernet2/4.702 unassigned YES CONFIG up up
Ethernet2/4.703 unassigned YES CONFIG up up
Ethernet2/4.704 unassigned YES CONFIG up up
Ethernet2/4.706 unassigned YES CONFIG up up
Ethernet2/4.708 unassigned YES CONFIG up up
Ethernet2/4.710 unassigned YES CONFIG up up
Ethernet2/4.711 unassigned YES CONFIG up up
Ethernet2/4.712 unassigned YES CONFIG up up
Ethernet2/4.713 unassigned YES CONFIG up up
Ethernet2/4.3411 unassigned YES CONFIG up up
Ethernet2/4.3412 unassigned YES CONFIG up up
Ethernet2/4.3431 unassigned YES CONFIG up up
Ethernet2/4.3432 unassigned YES CONFIG up up
Ethernet2/4.3433 unassigned YES CONFIG up up
Ethernet2/4.3434 unassigned YES CONFIG up up
Ethernet2/4.3435 unassigned YES CONFIG up up
Ethernet2/4.3436 unassigned YES CONFIG up up
Ethernet2/4.3499 unassigned YES CONFIG up up
Ethernet2/5 unassigned YES unset up up
Ethernet2/5.102 unassigned YES CONFIG up up
Ethernet2/5.105 unassigned YES CONFIG up up
Ethernet2/6 unassigned YES unset admin down down
Ethernet2/7 unassigned YES unset admin down down
Ethernet2/8 unassigned YES unset admin down down
And all of the sub-interfaces are on-line, working properly, etc.
Hi Ron,
It happened to me and the solution was created a permit icmp rule to the interface from any-ipv4. After that, I was able to ping IP address belong to this interface.
> show arp | include 10.162.20.1
LM_INT_PROD_VL2103_APPL 10.162.20.113 0050.5688.b3f2 14
LM_INT_PROD_VL2103_APPL 10.162.20.105 0050.5688.93c7 136
LM_INT_PROD_VL2103_APPL 10.162.20.107 0050.5688.5567 346
LM_INT_PROD_VL2103_APPL 10.162.20.103 0050.5688.1afc 556
LM_INT_PROD_VL2103_APPL 10.162.20.104 0050.5688.2e8c 556
LM_INT_PROD_VL2103_APPL 10.162.20.102 0050.5688.9882 556
LM_INT_PROD_VL2103_APPL 10.162.20.101 0050.5688.4fd7 1276
LM_INT_PROD_VL2103_APPL 10.162.20.106 0050.5688.916d 1306
LM_INT_PROD_VL2103_APPL 10.162.20.100 0050.5688.70cc 1306
>
>
> ping 10.162.20.113 repeat 100
Type escape sequence to abort.
Sending 100, 100-byte ICMP Echos to 10.162.20.113, timeout is 2 seconds:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (100/100), round-trip min/avg/max = 1/1/10 ms
>
Something like this.
So you have IP’s on all those subs? not sure why they don’t show up here. You can also try show interface inside or whatever the zone name is….however, you CANNOT ping from one sub to another, FTD does not allow that, so that is the issue your probably having. I don’t know why that is not allowed, I just know it is now…
So you have IP’s on all those subs? show ip address | include Ethernet2/4.300
Interface Name IP address Subnet mask Method
Ethernet2/4.300 INTERFACE-NAME 10.216.114.1 255.255.255.128 CONFIG
you CANNOT ping from one sub to another, FTD does not allow that ping 10.216.114.141
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.216.114.141, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
> ping interface INTERFACE-NAME 10.216.114.141
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.216.114.141, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
Should i quit to my job or simply this isn’t not right? ;)
So you have IP’s on all those subs?
Yes sir, for example:
show ip address | include Ethernet2/4.300
Interface Name IP address Subnet mask Method
Ethernet2/4.300 INTERFACE-NAME 10.216.114.1 255.255.255.128 CONFIG
you CANNOT ping from one sub to another, FTD does not allow that.
Yes sir, i’m aware of that. I only want to ping the subnet IP addresses.
Example:
> show arp | include INTERFACE-NAME
INTERFACE-NAME 10.216.114.141 AAAA.BBBB.CCCC 2
>ping 10.216.114.141
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.216.114.141, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
> ping interface INTERFACE-NAME 10.216.114.141
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.216.114.141, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
Should i quit to my job or simply this isn’t not right? ;)
No don’t quit your job, this isn’t that important of an issue! :)
You can ping your physical interface IP, but not your subinterfaces, ever. That’s just the way that is.
HI Todd
I can ping my interface on the firewall from the inside.
however i cannot ping the router or the outside interface of the firewall.
i have enabled the Platform stetting’s ICMP
You cannot ping through an FTD device by default, you need to create an ACP rule to allow it
I can ping to my interface gateway in same network but cannot ping other interfaces gateway in FTD.
Todd said – You cannot ping through an FTD device by default, you need to create an ACP rule to allow it
I suspect an ACR is needed to ping across FTD to other gateways.
You cannot ping from one sub interface to another, that’s just how it works (assuming you were trying that)
Will the rate-limiting I implement on platform settings apply to the ACR allowing ICMP through? Or is there another place to implement ICMP rate-limiting?
You can do rate limiting with the QoS Policy in the Devices section for layer 3-7
Thank you for the response !!
I’m still confused. Could you please tell me the steps to allow ping across to interface gateways ?
Hi Todd. I have an issue with the Cisco Firepower 2120 device. I have things setup to the point that users from my inside network are able to access external resources but i am not able to grant access to users from outside my network to access a Server hosted in my inside network. All permit Access-lists doesn’t seem to take effect.
What do you suggest i do please?
Hi, after attempting from the outside, look and search on Connection Events for what rule blocked those packets, and then move your new rule above that rule.
Thanks for the reply. The Strange thing is that the only policy identified by the Firepower Appliance is the Inside_to_Ouside Policy. I placed the Outside_to_Inside policy above the Inside_to_outside policy, only the Inside_to_ouside policy still takes effect.
I checked the Connection events as do not see a match for any denied traffic. It is as though the policies are no existent but they are there.
I can share the config if you dont mind.
Bad thing is that the firepower device does not have command line like the Cisco ASA firewall where I am able to hardcode every configuration and can be in more control of the appliance.
I have been on this for over some days now.
You can by using the Cisco API, but no direct CLI is a drag for sure.
What are you trying to do? How can I help?
So sorry i didnt get to see this reply uptil now.
Not sure why, but we bought a Cisco Firepower 2120 Appliance to replace the existing ASA 5510. I was meant to transfer the configuration and functionality on the existing ASA device to the firepower appliance. This includes connectivity from inside of the network outside (To the internet and to a remote site), connectivity from outside of the network to inside to access specific servers in the 192.168.0.0/24 subnet.
After my setup, users are able to access the internet and also get to the remote site over the VPN setup on the Internet edge routers between both sites. However, users are unable to access the internal servers on the LAN.
I have done allow policies from outside to inside but no luck.
This is my 4th week working on this
My resolve now is to get the compatible ASA image for the FPR2120 appliance and load on the firepower appliance so that I can configure the appliance via command line.
I could use your help if you can point me to where i could be wrong.
Regards
Strange things again is that when i check the connection events for traffic flow and see if some policy is blocking my traffic from outside, i realize that only the Inside_to_Outside rule is recognized. There are no matches for every other rule i have created.
since you just bought the system, you should call cisco and ask for their help.
also, you can run ASA on 2100 with no problem!
Thanks a lot for your support.
Will do as guided.
Thanks
Hi Todd, my FTD is working fine and i can ping the internet from any computer inside the network but the weird thing is that i cannot ping the Inside Interface IP from any computer from the local lan. i also can ping any computer from FTD cli which makes it more weird. is there any config i missed on this one?
You either have sub interfaces on the interface, or a Platform policy is blocking ICMP on the inside interface
Thanks for the information provided! we will use this information into our GPT/Chat-GPT dataset