How to find the list of IP, URL, and DNS entries in the Cisco Firepower Feed
Customers and students always ask me how to see what is in the Firepower objects updated by the Cisco feed, so this blog will show you how to find this information.
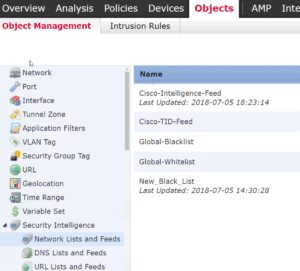
Security Intelligence is an object category that contains three different types of objects. These are:
- Network
- DNS
- URL
You can find and manage all the feeds in the Objects page:
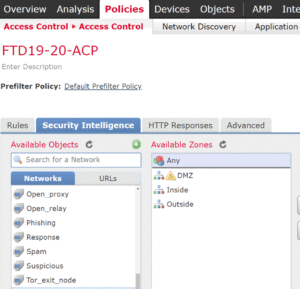
The Objects are implemented in the Access Control Policy under the Security Intelligence tab:
Finding the IP addresses in the for the Network Lists and Feeds objects
Nicely, this one is pretty easy. Go to Talosintelligence.com and click on Reputation Center and then IP Blacklist Download
The huge list of IP’s in the Network objects will appear. Now press CNTL-A and then CNTL-C.
Open Notepad on your desktop and then press CNTL-V and the list will populate into your Notepad; save the file.
Now you can just use those IP’s to test your SI lists by pasting these IP’s into a browser from an inside host.
Finding the URL and DNS addresses in the URL and DNS Lists and Feeds objects
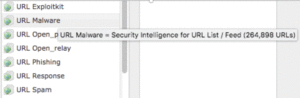
Inside the ACP Security Intelligence tab, you can hover over one of the Network, DNS or URL categories. A pop up will indicate how many entries are currently in this category.
That’s great, but what about the actual entries in each of these objects?
To find these you must SSH to either a FTD device or the FMC. You will find the three types of security intelligence entries in the following three locations:
- Network– /var/sf/iprep_download
- DNS– /var/sf/sidns_download
- URL– /var/sf/siurl_download
Here you will find separate text files for each security intelligence category. You will also find text files for any of your custom feeds as well.
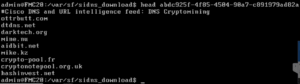
Here is an example of finding the DNS feed file by using: cd /var/sf/sidns_download and then listing the files using ls
The files have unrecognizable UUID (Universally Unique IDentifier) names but if you use cat, head or tail to look at their contents you will see they are simply text files. Each one contains the name of the list as a comment in the first line.
Using this technique you can find out the contents of any of the security intelligence download files for each of the three categories. One huge caveat however, these files are updated frequently. Depending on the update frequency you have selected, an entry that was here 5 minutes ago may be gone now. If you’re trying to troubleshoot an issue or predict whether a given IP, domain or URL will be blocked this may not be a viable technique.

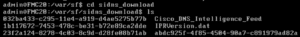

How can I tell what url the default feeds are using as I am unable to see any objects in the SI tab (both network and url) in an ACP.
I am behind a proxy and they have allowed access to intelligence.sourcefire.com but are seeing no hits even though i have frequency changed to 30mins. However they have denies from my FMCv to feeds.feedburner.com not sure what this is.
Thanks
do you have a device in the FMC? The objects don’t show up until you have a device registered with the FMC
if so, then you don’t have internet access to the FMC
feeds.feedburner is not cisco, it is something else that someone set up statically there
Thanks Todd,
I have a device registered to the FMCv and a simple ACP associated but the device is not licensed yet, waiting for the customer to sort the licensing out.
That feeds.feedburner is strange one because this is a new installation on an ESX box so it’s got the default feeds.
Will wait for license and then hopefully the objects will show up.
Thanks,
No License no feeds.
Awesome! Thanks Todd!
I am using FMC with no internet connection. There is Global Blacklist for URL and Global Blacklist for DNS are configured under the policy. How do I prove that it’s block the DNS or URL from a non internet computer. I tried nslookup and ping but that did not generate any event under Analysis. Can you please help?
you can go to Talos and pull down the IP blackist, then you just use one of those IP’s on your internal computer and it will block it when it gets to the FTD device
Actually I have a blog on this….
Hi Todd
Where do the custom uploaded url lists go?
Please forget my recent comment. I just couldn’t find the custom ones. I can now….
Has Talosintelligence.com Reputation Center removed the option for IP Blacklist Download? I do not see it anymore
yes, its now at snort.org.
scroll right and you’ll see a small download link
Where can I download IP Blacklist now ?
I can’t find a small download link in the Reputation Center
They moved it to snort.org
Its under Downloads.
hi todd, i know the fmc download the list from the web url’s , but do we need to do a deploy to push the configs to the FTD’s? or everytime there’s an update on the feeds it also automatically updates the FTD’s list? thanks for all the help
by default the list is downloaded to the FMC and pushed to the FTD’s every two hours. You can change that to a lower time frame in the Objects.
If you add your own list to the SI then you need to deploy, the cisco objects are pushed after a download by default, so no worries!
Todd