How to Find an Original Source IP in Cisco Firepower when the hosts are behind a WSA
You can find this new book on Amazon:

If your WSA is configured to send original client information, you can find this very useful information in the FMC Analysis>Connection Events output, and make rules in your ACP using this information.
To find an original source IP address of hosts located inside the FMC connection events output, but the hosts are behind a WSA for example, use the following steps on your Cisco FMC:
1. Go to Analysis>Connection Events
2. Click on the Table View link
![]()
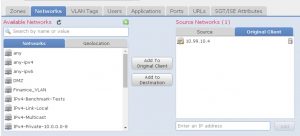
3. Click on any of the the black circles where you want the new column showing the original source IP’s to appear:
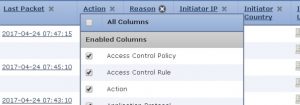
Notice the new entries available to either delete or approve as column for this view.
4. Scroll way down until you find Original Client IP and choose that option.

5. The new column will appear and show you the original client IP addresses behind the WSA, as shown in this example.

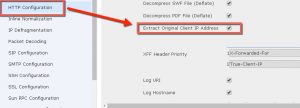
6. If your IP’s don’t show up, go to your HTTP Preprocessor (found in the Network Analysis Policy) and make sure that Extract Original Client is enabled, which in Firepower it is on by default now:
7. Now, starting in Firepower 6.1 code, you can make rules using the original client IP’s where the source address is the WSA and the original client is the source IP found in your Connection events: