RDP Error 0x609: Cisco Releases New Snort Update 5/24/19; Brings down RDP access with Error 0x609. Here is how to fix this…
A whole bunch of RDP users starting losing connections with RDP Error 0x609 when traversing Cisco Firepower Snort because of an update that was sent out by Cisco Talos.
Here is how to fix this without disabling your entire IPS inspection.
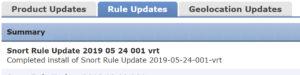
First, here is the update that caused this issue:
let’s take a look at the rules that caused this issue.
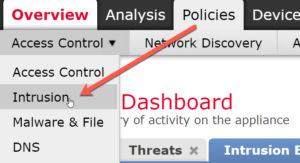
From your FMC, choose Policies>Intrusion
Open your IPS policy by clicking on the Pencil on the right hand Side of your IPS policy
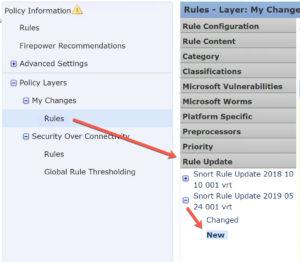
Now go down to Policy Layers> My Changes>Rules and then scroll down on the rule accordion to Rule Updates
Click on the newly installed update and then click on New
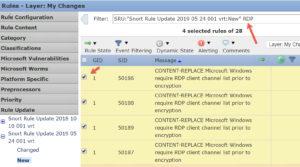
In the Filter Bar, add the letters RDP to the end of the current search and from 7 to 28 rules will show up, depending on your rule set.
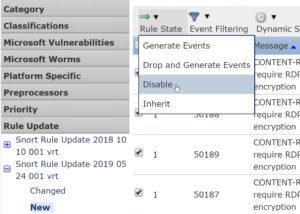
Click on the top four rules (SIDs: 50186-50189), then go to Rule State and choose Disable.
Save your Policy and redeploy. This will skip inspection for those four rules, but you will still have inspection for all other enabled rules.
The four rules have content replace keywords in them. I believe they were made to modify the RDP handshake to allow the original rule to actually see the exploit. This was replacing the content in all RDP connections.

Thanks for the fast and relevant post on this!
You’re welcome! This is my everyday pretty much now!! LOL
This one was pretty easy…
Appreciate the post!
Todd, I have a client reporting this issue but the listed SIDs are not present on the SRU update for 5/24/19.
yes, cisco sent out a new update that deletes them….they did this late Saturday afternoon I think. They probably just have to redeploy
let me know!
Snort/Talos Rule update 2019-05-24 looks to be the problem. If you download 2019-05-25 (just released) it looks like it resolves the issue.
For Firepower — Updates / Rule Updates / One-Time Rule Update / Download Now / Import — Then deploy policies to sensors and you should be good.
Thanks Michael, yes I am sure they’d put out an update for this…thanks for the helpful post!!
You saved my day.
That’s great to hear! Thanks for posting!
Michael, thanks for the post.
How do I open the IPS policy on Windows 10 Pro? is this “Local Security Policy” application?
this has a wizard to create new IP security policy, but the note there says: The default response rule is supported only on computers that are running Windows 2003 and Windows XP.
Appreciate your response.
Alex, this isn’t a Windows problem. this is a Cisco ASA and/or Firepower problem, and the issue can be fixed in the Firepower management center as described in my post here. Hope this helps
Thanks for the information!
You’re welcome!
Thanks! You saved my day!
Great! Glad it helped!
where is Cisco’s official KB on this ?
https://community.cisco.com/t5/security-documents/firepower-drops-rdp-traffic-after-sru-rule-update-2019-05-24-001/ta-p/3862835
Awesome.
Maybe “sort” in title should be “snort”
yea, read that 20 times and didn’t see that!
Is there a way to view these disabled policies? I disabled them (thank you!) and it fixed my problem, but I’d like to locate them again in my rules. I can NOT see there anywhere. Under “My Changes” or “Balanced Security and Connectivity”, etc.
Hi Ryan!
Cisco sent out a new update that deletes them, so that is probably what happened. They kinda did this silently in the background.
if you go to the filter bar and type in on elf the SIDs and it doesn’t show up, then it’s been deleted by Cisco’s update