Cisco FTD SSL Policy Crashes FTD devices with Application Bypass Errors…
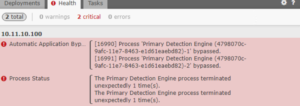
If you’ve never seen an Automatic Application Bypass (AAB) error occur on your Cisco FMC, which means your SNORT is about to restart, then this is a way to get experience with such an error, although I doubt Cisco had this in mind for their SSL policy and Firepower. Understand this isn’t only a “Cisco” or “FTD” issue; it will happen on any SSL configured type device if they go to certain public pinned sites, but it sure made for a great headline, and you can reproduce this easily.
First, you need to go to each individual Firepower or FTD Devices tab and enable the Automatic Application Bypass Feature (AAB). I usually enable this for all my customers, and it just became available for FTD with 6.2.2 code.
Enable the process below at the bottom of the Devices screen:
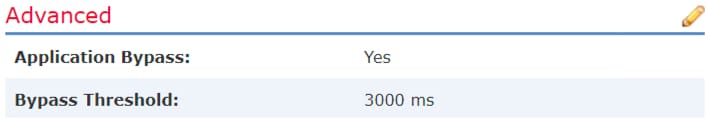
If a file is being compared to a snort rule or group of rules and it can’t make a decision on the file in 3 sec (by default), then Firepower will let the file through uninspected.What this means is that your Snort process got hosed/stuck, etc and after 5 minutes it will restart the snort process and then try it again…
The AAB isn’t an error you want to see in your production network. If you are not using the SSL policy and receive this error more than once, you need to call Cisco stat!
If you are doing a basic Decrypt PKI on the FMC, and the the FMC PKI issues the certificates for each host to look at HTTPS traffic this is something to think about here:
For your FTD deployed devices, Google’s (or any) public-key-pinning solutions for their Chrome browser is a serious issue for you (http://www.zdnet.com/article/google-chrome-is-backing-away-from-public-key-pinning-and-heres-why/)
(HPKP) is an IETF standard that Google engineers wrote to improve web security but now consider harmful (ya think?).
Configure your SSL policy and deploy, and then from an Inside host, use Chrome and www.google.com and viola! Application Bypass errors galore…
To fix this, you need to remove your SSL policy and reboot your FTD device(s). Better yet, just make sure none of your users use Chrome and then goes to google.com, right?