Cisco Firepower Threat Defense (FTD) devices are expensive! Which one should you get?
This post goes hand-in-hand with my FMC blog
Cisco FTD devices are expensive!…and they are announcing new more expensive one’s next week…here are the current as of right now:
Cisco’s 2100, 4100 and 9300 FTD Devices
So which one of these expensive FTD devices do you need?
Did you know it’s actually pretty easy to figure out the FTD device(s) you need for your network?
Only one small caveat to this easy way is that you need a CCO login and then access to page ngfwpe.cisco.com
Most of you probably already have this access, but ask your rep if not. This is what your rep will use to determine on what to sell you…if he says you can’t have access (BS), then tell him you want to watch him perform this…
Here is the home page of ngfwpe.cisco.com after logging into Cisco.
First pick your threat inspected throughput wanted/needed for your network:
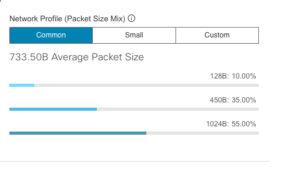
Then choose your typical network packet size on your network, or leave default
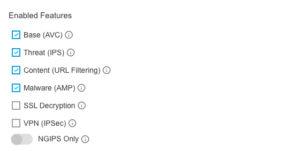
…Most importantly, add Enabled Features:
It’s best to keep clicking on various features to see different products suggested…
IMPORTANT NOTE: Let me stop and discuss the Features listed above. I actually had a customer that didn’t buy any licenses for any features. This means you’ll only get Base licensing (which is included by default), so they couldn’t add any SI, IPS, Malware or URL. At a minimum you NEED Threat licensing, which provides Security Intelligence (SI) and IPS capability. If you don’t want to buy at a minimum Threat, then just go to BestBuy and buy a NetGear Firewall for $50.
Now add the typical network utilization you think you’ll use…I usually click on the <40 to get as many possible solutions shown as possible
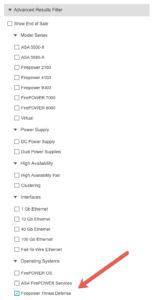
In Advanced choose the model you have or are possibly thinking of getting:
Add other filters, such as OS. However, I just typically click on FTD to make it easy…
Now, go to the top and click APPLY.
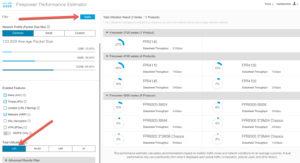
In the following output, I had filtered on 1Gbps inspected throughput, common packet size, <40 Utilization, Base, IPS and URL filtering, and then choose FTD OS.
You can see the 11 hardware devices that it is suggesting…
Just keep adding filters to narrow down and find your device! It’s actually fun to see what Cisco comes up with on your filters.





Strange. When I try to access that page I get a “Policy Error; Access Denied” page.
humm…can you try it again?
I’ve tried it multiple browsers and can’t find an issue, but will work on this!
thank you for writing about this, and I look forward to your reply!
I tried Chrome, FF, and Edge (scary…I know). Also tried on my iPhone on wifi and LTE and get the same screen/error. I’ll try from home tonight too.
You are talking about the cisco link in the blog! Yes I mention in the blog you have to have access. Talk to your rep!
I think it has something to do with the privileges of your CCO ID. I am getting the same error but it’s only after logging in. It also did it for me during a recent class you taught. Sometimes Cisco makes their content for only partners or just non public. I’ve had them change some of their tools in the past to allow access with a basic CCO ID.
Thanks Robert! yes, you have to have access to that site…
it’s a great site, but you have to request access.
Looking at the block diagram of the 9300 above you see that the supervisor has its own CPU and RAM for controlling the operating system (FX-OS), which is used to deploy Firepower Threat Defense or ASA software to a security module and manage the network interfaces.