Cisco Firepower FTD BitTorrent problem
Are torrents bad? Wow, yes! One of first few rules in the ACP created for all my customers have to do with torrents. Torrents are a horrible thing on any network, even if only one host has it!
I’ve been telling my clients and students for a long time about BitTorrent issues with Cisco Firepower/FTD. Cisco finally admits that they can’t read the BitTorrent handshake correctly with the File policy. In this very short blog, I’ll show you the best workarounds for this.
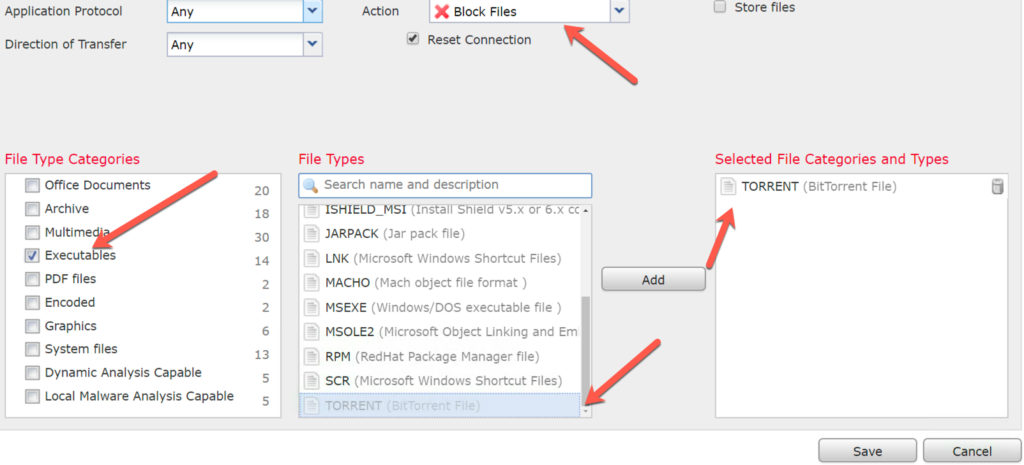
You can use a block rule for peer-to-peer categories in your ACP, which works well for all type of torrents, and the Torrent category in your File Policy, however, the File policy is hit and miss (more miss) on torrent streams because of the handshake issue, which is why I use the peer-to-peer Application or URL categories, as well the File policy:
Here is the File Policy torrent rule I use at ALL my clients:
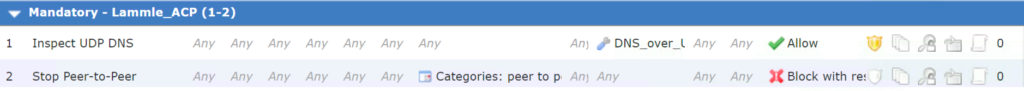
here is the first two lines of almost ALL my ACP’s I configure:
You can use either the Application or the URL in the rule, but don’t use both.
-You need to have a clear security policy that forbids torrents of any type!
…and here is an announcement (finally) from Cisco on this:
Cisco Firepower System Software BitTorrent File Policy Bypass Vulnerability
Medium
Advisory ID: cisco-sa-20180207-fss
First Published: 2018 February 7 16:00 GMT
Version 1.0: Final
Workarounds: No workarounds available
Cisco Bug IDs: CSCve26946
- A vulnerability in the detection engine of Cisco Firepower System Software could allow an unauthenticated, remote attacker to bypass file policies that are configured to block files transmitted to an affected device via the BitTorrent protocol.The vulnerability exists because the affected software does not detect BitTorrent handshake messages correctly. An attacker could exploit this vulnerability by sending a crafted BitTorrent connection request to an affected device. A successful exploit could allow the attacker to bypass file policies that are configured to block files transmitted to the affected device via the BitTorrent protocol.There are no workarounds that address this vulnerability.
—————————————————————
Hello Todd,
How would you block torrent on a cisco 5585x ver 9.6…
Are you running ASA with Firepower? You can create an ACP rule that blocks the Peer-to-Peer application.
No am not running firepower…I heard it uses a lot of resources. How and where do I create ACP rules your tutorial is not clear does it goes for ASA? Do I need to run firepower and how is it enable…Please if possible send me the instruction for ACP…I just want to take the time to thank you for your Sybex CCNA books, studying it alone help us to pass our CCNA.
Well you need my book on Firepower, class or even my video series on my site
it runs a snort process as a module, and whoever told you that it used a lot of resources probably didn’t know what they were talking about
it uses what you configure
When I add DNS_over_UDP to the Dest Ports, I get a warning “Configured ports will prevent the File Policy from being triggered. I believe I have the exact BitTorrent file policy you list above. I am running 6.4.0.7, have the BitTorrent file policy, and the two mandatory ACEs in the ACP. My URL filtering license just expired, but I wouldn’t expect it to affect the ACP as I am not using URLs in my ACE and I am using the Application Categories: Peer-to-Peer.
if your using the Application tab, then the URL is not relevant. There is something in your rule that isnt’ quite right. I have not see that error again, so can you screen shot some of this and send it to me? [email protected]
I’m really interested.
Hi Todd, I have captured the screenshots of the policy error but I can’t load them here. I will reach out via LinkedIn.
Okay
Hi Todd,
This is very useful, thank you.
I see you have Block with reset action for P2P application rule in the screenshot.
In this set up, you can’t select the file policy, so do you have another rule for file policy rule?
As the Block action will disable Intrusion and File policy selection so assume you have to have an ip any any Allow rule with this torrent File policy, and the File policy will drop Torrent Executable?
Many thanks!
yes, that’s correct, at the end of my list there is permit ip any any with IPS and File inspection on the inside to outside zones
Thank you for confirming.
I noticed something strange however, after following your ACP example which has udp/DNS inspection and P2P block with reset rules in the mandatory category, packet-tracer results are a bit off and it seems everything is hitting the P2P block policy and get ALLOW action, and not the actual intended access-list.
I guess it makes sense as it’s using ip any/any but this makes trouble shooting a bit challenging. Any recommendations?
Please advise.
Many thanks,
Hi,
I need image to Cisco FMC to run on VMware please .
Thanks