Awesome Highlights of Cisco Firepower 6.2 – Packet Tracer and More!
Let’s look at a few of the interesting new features in Firepower 6.2. This release isn’t big on “wow” factor, most of the changes are incremental feature improvements. One of the biggest new capabilities is inter-chassis clustering on the FP9300 and FP4100 series devices. Previously, you could only cluster the three service modules on a FP9300 within the same chassis. This was called intra-chassis clustering. With 6.2 you can now create a cluster of up to six modules across two FP9300 chassis or across six FP4100 devices. If you needed the additional inspection power or redundancy of multi-device clusters your ship has come in!
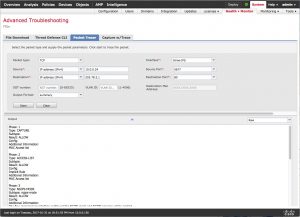
While clustering is cool, it may not be something that everybody needs. The next new feature is something many customers will find useful from time to time. You now have Packet Tracer capability in the Firepower Management Center (FMC). What this means is you can now trace an imaginary packet through the system and see where it might be blocked. This can even be done without any type of event logging on the FMC. While 6.1 provided access to the packet-tracer command, 6.2 goes a step further and provides a full-blown packet tracer UI on the FMC! The idea is that you input the type of packet, source/destination IP and ports then the system will show you what happens to this packet as it passes through the device.
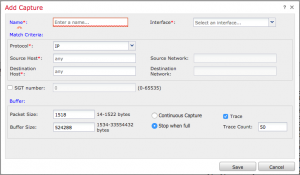
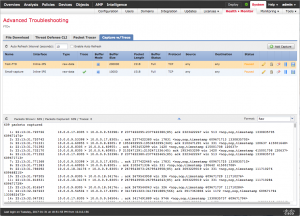
The other feature with a massive coolness factor is Capture with Trace. Like the Packet Tracer this is available without dropping to a command line and provides the ability to perform a device packet capture right from the FMC GUI! This can make troubleshooting much easier and faster by providing an easy way to grab a packet capture without the necessity of looking up the command line packet capture syntax. You can select the interface, source and destination hosts, capture buffer size and even the Identity Services Engine Security Group Tag if desired. After the capture is finished you can download the ASCII or PCAP formatted data and analyze it further in your favorite traffic analysis tool.
Snorty says, when it comes to troubleshooting custom Snort rules, packet captures are extremely valuable!

Snorty
I can see the Packet Tracer interface but it is greyed out. Is there a feature set I have to enable, & if so, how do I enable it?
what type of FTD devices is it? What code?
On a FP9300 inter-chassis cluster of two chassis and one security module each, can you do a capture for the cluster? I can do captures for each individual module, but I don’t see a way to include all modules in the cluster. We are using 6.4 code.
yes, you can do this now…it’s in this document:
https://www.cisco.com/c/en/us/support/docs/security/firepower-management-center/212698-configure-ftd-clustering-on-fp9300-intr.html#anc12
I am running SFR module, I don’t see packet tracer option.