Cisco Released Firepower 6.5 Code with New Intuitive Interface
Cisco has released a new code for their Firepower devices and the first thing you’ll notice is how they updated the login page, which is a nice change from the legacy.
Be forewarned that the new 6.5 code uses a new hardened password and it cannot be recovered, so be careful here!
 Next, you will be asked if you want to license the device, but that’s it – no more time consuming configuration before you are let into the FMC. Why? The reason you had to configure the FMC with DNS addresses and search domains in previous codes is because they had the NTP server of the FMC set with a hostname and still do, so the NTP name had to be resolved. In 6.5 they have added the Umbrellas IP address in the FMC management settings, which solved that issue and we no longer need any pre-configurations. This makes logging in the first time to a new FMC at least 10 minutes faster.
Next, you will be asked if you want to license the device, but that’s it – no more time consuming configuration before you are let into the FMC. Why? The reason you had to configure the FMC with DNS addresses and search domains in previous codes is because they had the NTP server of the FMC set with a hostname and still do, so the NTP name had to be resolved. In 6.5 they have added the Umbrellas IP address in the FMC management settings, which solved that issue and we no longer need any pre-configurations. This makes logging in the first time to a new FMC at least 10 minutes faster.
One of the nice features is the new dropdown menus that are easier to traverse than the legacy screen. Here is a shot of the Analysis drop down menu.
However, once this novelty wears off, you’ll be switching back to the Classic screen which can easily be changed in the User / User Preferences
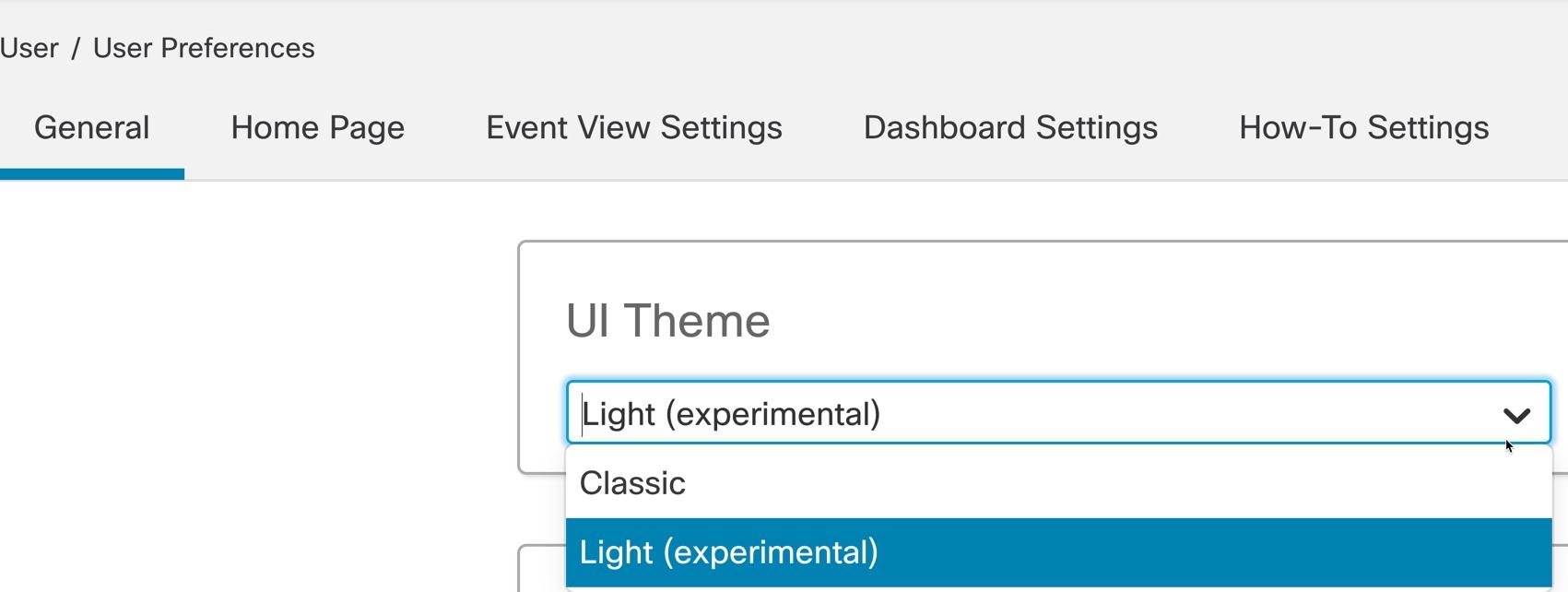
Why change back? Although the new GUI is intuitive and it’s easier to traverse in some or even most ways, it is for sure much, much slower, and if you work on the Firepower Management Center (FMC) even a few hours a week, you are already at your your wits limits with delays in the Analysis screens. However, be sure to check out the new GUI, which has been decided to be disabled by default for now.
So what’s deprecated with 6.5?
…well, the System>Integration>Identity Sources shows the following now, so it’s not gone yet:
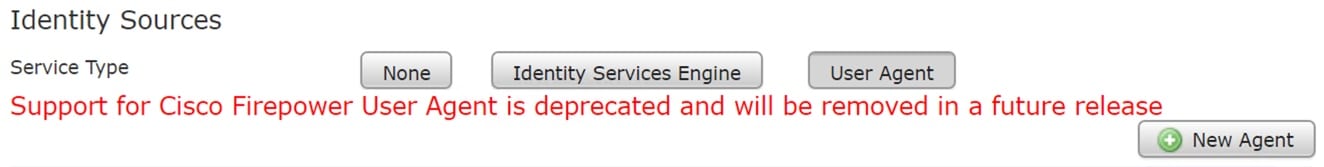
The SourceFire User Agent (also referred to as Firepower User Agent) is a mid 1990’s supplicant that worked well, but need to be replaces. I already have most of my customer on PxGrid and you should be as well, but I believe the Defense Orcastrater will also possible be a solution here.
So what’s are the new features with 6.5?
First and foremost, there is a great migration feature that can be used to transfer a vFMC to a hardware FMC, for example. This is long overdue! However, there is a big caveat here: You can only migrate to a new FMC such as 1600/2600/4600/v300…that is somewhat disappointing, but this is still a welcome new feature.

Secondly, there is a new URL Category and Reputation process now done through Talos and not Brightcloud, and it’s really good. I’ve tested this thoroughly and had no issues.
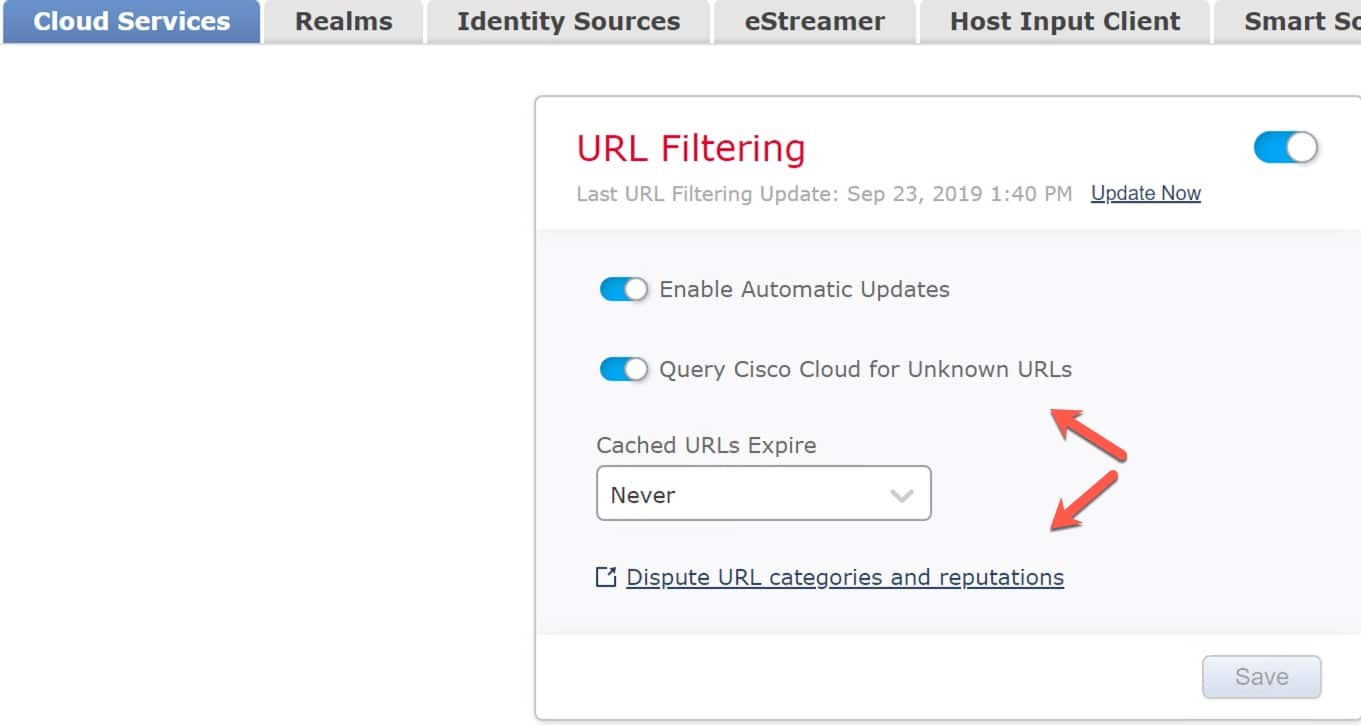
Notice that Query Cisco Cloud for Unknown URLs have been enabled since 6.3, but you can dispute a URL category and reputation, which I’ve had to do with Brightcloud for many customers and my own home page as well.
Now you’ll see the new Categories and Reputations listed in the URL tab on a rule in the ACP
In Connection Events the new URL Categories and Reputations are displayed
Now you can find all the new categories at talosintelligence.com. Go to Reputation Center and choose Categories. You’ll then get a list of all the Categories and the new Reputations listed, along with some sample sites for each Category as shown below.
So for me, there was not a lot of big changes from 6.4 to 6.5, mostly because I didn’t work on the new REST API, Firepower Device Manager (FDM) and ASDM updates, which is where the biggest changes are. I’d certinaly like to list more new features here, but this post is already getting too long…We did test a new snort version as well, but that was pushed out to a later version. Again, the migration feature from one FMC to a different FMC is a really great feature of 6.5.
In conclusion: I beat the hell out of 6.5 with my own production network that has 60 clients on it, and I can recommend this code. Understand that I tested this with the policies and configurations that I use at my clients every day. I tested every policy on the FMC throughly with 6.5.
UPDATE 10/24/19: There is a NAT bug in 6.5, so please be aware of this before you upgrade!
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvp70833/?rfs=iqvred
Here is what I used to test 6.5 code for about the last 3 months:
- Two Cisco 2500 FMCs
- Twenty Virtual FMC’s, half I upgraded from 6.4 and the other half I installed new
- Two (unnamed) FTD devices in HA with 10Gig links, and boy are these awesome devices! Cisco’s going to have to try and pry them out of my hands when they want them back! Can’t wait till I can tell you about them in Mid Nov.
- Dozens of virtual FTD’s, half I upgraded and half I installed new
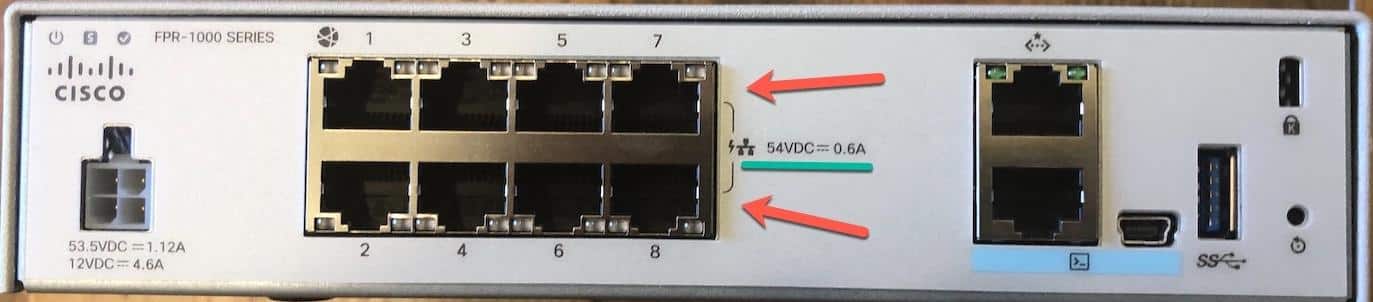
- Two FTD 1010’s in HA that are my favorite devices by far, and these little bad boys are going to change everything! These really needed to be out two years ago….On a 1010, each port can be either layer 2 or 3, has PoE, IBR, and up to to 60 logical routed ports for VLANs, subineterface, Etherchannel, and a lot more. I’m going to do a vblog on the 1010’s shortly….in the meantime, here is my awesome 1010…notice the two 0.6A PoE ports 7 & 8 on the right…
- Two 4140’s that really handles 6.5 with both FXOS and FTD with no issues. Powerful FTD boxes. Period.
Check out www.lammle.com for the latest in advanced Cisco products, videos and classes for Firepower/FTD with 6.5 code, ISE, IOS XR, AMP, the new NA/NP, Amazon AWS and more!

Hi Todd. Thank you for being so quick with this update.
There seems to be a lot of changes with regards to URL Filtering on FPR 6.5 code (new categories names, multiple categories splitted etc.) Do you know how FTD 6.4 or lower will work with FMC 6.5 with regards to these changes ? Could this cause some issues if we deploy policy from FMC 6.5 with new categories to devices running 6.4 ?
That’s a great question. From what I can tell, my 6.4 devices are still on bright cloud. I think in a new up date such as 6.4.0.6 maybe it will change, but let me check on that
Older versions managed by FMC 6.5 will continue to use Brightcloud. There are no plans to make this change retroactive to older releases. Hope this helps!
Jeff, thank you. That is odd for sure, but we appreciate the post!
Hi Todd
Nice to read your sum up of FTD 6.5. I agree that while it looks better with the new UI, it is far from usable and more painful compared to the old one. It just doesn’t look like its made with Frontpage 98 anymore, but that’s about it.
What I found a big point in the release notes of 6.5 is they are warning us already about the Firepower Power User Agent soon going byebye and we should be going over to ISE-PIC/Passive Identity.
I wish they would just give up FMC and focus on bringing CDO as an On-Prem solution (of course still has a lot missing and needs a lot of polishing) but the way CDO/SDC resp. FDM works with FTD is far better, compared to what FMC does.
#nomoresftunnel
I totally agree with the FPR1010 being a big change for Cisco, we really needed that FPR1010 (also 2 years ago ;) ). been working with the Layer2 Switch feature for a a while now and yes it is nice to have that function finally available. haven’t testet the PoE Ports yet.
Thank you for your comments.
I do believe they are going to use CDO. It’s useful now, and I heard it was going to go into beta for FTD…can’t wait!
But I use ISE with PxGrip with most of my customers anyway….
Any changes to hit counters? Currently hit counters are always reset every deploy, then they go back to “0”.
In the 6.4 and 6.5, the GUI hit counters are not reset, only the CLI (show access-list-config) and that still is reset
Todd
TrustSec with SXP and Destination SGT support are added to offer broader integration with ISE on FMC/FTD and FTD-API platforms. Please share your feedback, when you get an opportunity to review them.
Hi Todd. Is there a feature to migrate FMC configurations to another one, virtual to virtual? I’m trying to see if I can deploy FMC wthout having to do many manual configurations. I do some configuration with REST API as well as importing configuration files with policies. Some of the configurations and settings I would like to have deployed (aside from platform settings) are login banner, external authentication, backup profiles/jobs, etc. Does 6.5 offer features for doing this?
Yes, you can migrate from one FMC to another now – WITH 6.5 code….they must be the same code exactly, same VDB and same Snort version/date
Hi Todd, 6.5 for the FMC has been around for some time now. I went through the documentation here which clearly calls out that the target FMC model should be x600 for the migration script to run. Is there a way to migrate from FMC 1000 to a 4500 using the migration script on 6.5.0, or it only has to be x600?
In case this is not possible the only way would be to Import/Export policies and manual config for the rest. Will the manual deletion of device from source and addition to Target FMC impact HA for the FTDs, or impact the VPN tunnels running as we will have to recreate in target FMC.
You can only migrate to a 1600/2600/4600. I told them to allow to other devices, but they won’t do it
You’ll need to export and import your policies
When you bring your devices into the new FMC, you’ll have to configure the LINA process from scratch, so that is correct. Sorry! Yup, sucks..
Thank You Todd for a quick reply.
Hi Todd,
I am looking for the best way for migrating a HA Pair from one FMC to another considering minimum impact to network. Which would be more feasible with a minimum impact to network?
1. Break HA Pair and then move one FTD at a time to the new FMC
2. Delete HA Pair on existing FMC and disable HA manually on the FTD and then add it to new FMC one by one.
Rocky, you have no choice when moving an HA pair from one FMC to another.
You must break the pair, bring them individually into the new FMC, and then reconfigure them from scratch.
There are not two options available to you.
Good luck!
Todd Lammle
Hi Todd,
Thank you for all the replies. I cannot find option for port-channeling in FMC 4500 running 6.5.0 code in the GUI. Is there a way we can create port-channel on the CLI. Like merge eth0 and eth 1 to provide port level redundancy in the FMC.
Rocky, there really isn’t a way, hence the HA for the hardware FMC’s
the various ports on the FMC are actually used to separate data from event traffic if desired, or use the different ports on the FMC to manage different network FTD devices in a different IP range for example.
Thank you again Todd. That was really helpful.
Hello Todd. I really enjoy the content you publish in your blogs, very insightful and relevant. In the release notes for 6.5 there is reference to a FMCv 300. Do you have any insight to this new VMWare platform? I would also be interested to find out if you have any comments on the possibility of FMCv Hyper-V support? Thanks!
I couldn’t run it as I tried to put it on my server and it wouldn’t load. It takes a minumum of 64G of ram and huge amount of processing and storage…you might as well buy a hardware FMC! Don’t know about the Hyper-V support
Hi Todd.
I have a question regarding FMCv300 and hoping if you could provide some insight.
I’m in the middle of a huge deployment and we were waiting for this “stronger” FMCv to become available so that we could test it. The problem is that it is nowhere available on the CCO download section. Since you mentioned that you couldn’t run it (due to high RAM requirements), I was wondering how did you get access to the OVA? Is it publicly available?
Thanks in advance for your answer and for your great posts!
Hello, I am on the beta team so I have seen the vFMC300, but as you mentioned, I haven’t been able to run it. I don’t know when it will be released…soon though.
However, I don’t think this is going to make your network analysis faster, nothing will. The v300 power is for managing up to 300 devices with a virtual FMC.
If you have the current vFMC, then you can use 8 processors and up to 4TB of ram starting with version 6.5
Add more processing and ram to your current system if you can.
Thanks Todd, So with the current FMCv (max 25 device support) running code 6.4.0.4-34, I can set the VM to use 8 processors and up to 4TB of ram? what’s the max I can set the processor and RAM for FMCv-300?
Also with upgrading from current FMCv to FMCv-300 is it just a license thing and having 6.5 running or do I have to install a new VM (once released)?
Do you have a rough idea on the price difference between a FMCv300 and the FMC 1600 Appliance?
Thanks
I am still on 6.4.0.1. I have been hesitant to jump any higher because of all of the bugs people have mentioned. What is the highest stable release that people are using today? 6.5.0, 6.4.0.6 or what?
I think 6.5 is better than any 6.4 code, and I’ve been using 6.5 in production since it came out
Thanks Todd! Any bugs that you have noticed or know about? Have you seen it on a 2110 yet?
Also anything that I need to be prepared for with jumping from 6.4.0.1 to 6.5? Any changes that had to be made. Can I go straight from 6.4.0.1 to 6.5?
I think it is better than 6.4 for sure, and 6.5 fixed my HA issues with all version of 6.4
you can go straight from .6.4.x to 6.5 for sure
I ran 6.5 on 4140’s, 1010s, 1150s and vFTDs
Hello Todd
What HA issues have you encountered with FTD 6.4 that made you jump to 6.5 from the start?
Regards
Alex
UPDATE 10/24/19: There is a NAT bug in 6.5, so please be aware of this before you upgrade!
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvp70833/?rfs=iqvred
Version 6.5.0.1 is release but in the release notes this bug is not mentioned under Resolved Issues?
Sorry, which bug are you referring to?
Mathieu is talking about the NAT bug you posted for 6.5. Anybody jump on 6.5.0.1 yet? Any issues?
I won’t try 6.5 till next week now…thanks for the heads up
Alex, the HA issues were intermittent. My FTD devices would just start acting up and then finally just stop working. You had to reboot and then remove the pair to get them working again…ugh
Hi Todd,
Thanks for all the tips about Firepower.
I still don’t understand how and why there is no support for tunnel interface on FTDs since there are on ASAs.
Do you know if there is any way to configure BGP dynamic routing to Google Cloud via a VPN in FTD? In ASA I am running a Tunnel interface but again…no tun in FTD :(
Thanks, I hope you can help me understand this (or suggest Cisco to add tunnel interfaces in FTD :) )
Giovanni, I do not know the answer or if they support the tunnel you described. I will copy and send that to my contacts in cisco. Thank you for posting!
Hello I am totally new to FTD and just deploying my first box, what is the implication of not registering the box upon start up. Right now am on the 90 day eval, I don’t intend to use the firepower side of the software, just the firewall features. What features will shut down at the end of the 90 days. Thanks
I am not sure exactly what you mean by not using the Firepower side of the software. It’s all Firepower, right? So after 90 days it won’t let you deploy, but if you configure the FTD box through them FMC and deploy now, you can turn off the FMC and the FTD will still be working. You won’t get network analysis or malware lookups, but SI, URL filtering and IPS will still be working on the FTD. However you want the FMC for understanding your network, so after 90 days you can just build another FMC. This all precludes that you are just using this for training and not in production of course.
Thanks for all the testing and sharing of info you provide. Any update on the “unnamed” FTD device you said you could comment on in Nov?
Hi Matt, your email came out right when they released it.
it’s an awesome 1150 box, that has 10G interface, in a small compact form…I have two that I won’t give up!! :)
https://www.cisco.com/c/en/us/products/security/firepower-1000-series/index.html
Could you possibly comment on what you like about the 1150 so much and if possible give some comparisons to the 2120 which has similar throughput specs but drops the SFP+/10G interfaces? Trying to decide on higher end new model line or lower end older model line seems challenging minus the pricing difference.
Hi Louis, thank you for writing. There probably is not a lot of difference as you say between 1150/2140 or 50…as a matter of fact, I think they overlap and it confuses me on why cisco would do that, but no one had an answer to me on why that is…. So, to start with, I had to run my 4140’s to get the kind of speed that I now get with my 1150 pair, and they are about 1/4 the size or less than the UCS chassis models. The pair easily fit in my production rack with one management ethernet and two fiber SFP connections for each FTD device, taking up little room, but are speedy and consistent. To be fair, I think I was comparing them to the larger models and the rack management, not the smaller 2100 series. However, I had a 10 gig switch and was able to finally use those ports, so that was nice too. The 2100 and 1150 are similar in CPU specs and throughput, no doubt, but I like the 10 gig ports and the small form factor
thanks again for writing!
Todd
Any insider info on FMC 300? It’s been some time since they announced with no follow up.
Hi Anthony, yes, it is available now, but I have never run it because my servers won’t even install it. I have to buy a new server and at that point, I might was well buy a FMC appliance….but that said, I’ll be getting my new server next week and will try it anyway! I have zero customers with interest in it at this point. You?
We are looking at it because we have a stretched HA datacenter design with ACI Multisite between two physical sites. Because we deem it to be a Tier 1 workload and want the ability to move it and be highly available in a HA/DR scenario, virtual seemed like the path of least resistance. Any thoughts?
Hi Anthony, that’s not what they are designed for, so I do not recommend this. However, I have customers that do this and it does work, but Cisco does NOT support that design.
Why the vFMC300? how many devices do you have? the vFMC300 is not better than any other FMC, it just manages up to 300 devices….it’s not faster. The vFMC 25 version now supports 4Tb of ram starting wtih 6.5 code…
We are approaching the sensor limit of 25 and anticipate surpassing it. We’d only push the FMC to the opposing datacenter in dire circumstances – a true lights out DR scenario. When might it be time to also consider CDO? Do you anticipate prime time readiness down the road?
NO on the CDO…I beta that for Cisco and you don’t want that yet…trust me. I see some business use in the future for CDO…
Also, you may consider buying two 2600’s or 4600’s instead….you really don’t really want to run 25 on the vFMC, it really just can’t handle it…the vFMC300 will work, but I think the cost could be prohibited or equal to the hardware at this point…the amount of process and ram it uses means you may need a new server, and at that point the 2600 may work for you for the same price point, but you’d need two…so there’s that
Hi Todd,
What version would you recommend to run in 2130 box with FDM. Any known issues that I have to be worried about in advance? Specifically HA or NAT issues?
6.5 works very well for me, just use the latest update with 6.5 and you’ll be fine!
We migrated to the FMC 300 and can report that the v25 to v300 migration process is relatively smooth. The guidelines and steps work, though, we did have to reboot once following the sf_migration.pl script before we could proceed with licensing (smart licensing took a while) up the target FMC. It was just sluggish for 2+ hours and bouncing the box cleared that up. Once we did that final reboot the FMC came up and was noticeably smoother and more responsive for ops. In retrospect, we probably should have addressed this sooner. Though they are advertised for up to 25 sensors, if you are running 20+ on the v25, you are committing yourself to watching paint dry for hours on end in your day to day ops.
Will report if we have any issues, but this production instance seems to be all good.
I agree on the 25 limit, it shoudl say more like 14 limit for vFMC25
how much processing and ram are you using on the vFMC300?
32 CPU, 128GB of RAM allocated. CPU seems underutilized but memory consumption sometimes peaks out at around 90-95GB. Very very smooth though logging in and doing work this AM. We’ll see how the Light U/I performs for a while. It was completely unusable at v25 spec.
By the way, have you used the change management / reporting feature? I glossed over that feature but found it now and like it in principle when you have different hands in the pot making changes.
Hi Anthony.
I’ve also run the migration script and went from an FMVc25 to FMCv300. The migration run without any issues but now we are facing a licensing problem. After the migration, we’re getting an error on our Smart Satellite server that we’re missing FPRMCv-300-DEV licenses. This license is nowhere to be found on the official Cisco doc. Have you faced similar errors in your case?
Thank you in advance
Kostas
Good day Todd I hope this finds you well
I recently purchased NGFW2100 series and seems as if I can only manage the device via FDM, not FMC how best can it be managed via FMC please advice
Any 1000/2100/4100/9300 can be managed with either FDM or FMC. From the device command line (CLI), type:
configure manager local to managae via FDM
configure manager add ip_address_of_fmc passphrase to configure via FMC
Are you talking about the Change Reconciliation in System>Configuration? Yes, I use that at all my customers because it provide really good code information on the system in case you need to a restore…I run it every night, but i don’t really use it for anything else
Hi
Tod , When you recommed 6.5 , FTD or Sourcefire code on devices could be still 6.3 .
Sincerely
Viral Patel
yes, absolutely, the latest 6.5 code is stable with more features. That’s all I use
thanks,
Todd
Hi Todd,
Thanks for all the info you give, just an OT here speaking of Firepower versions and releases:
I heard that code 6.6 or 6.7 is going to add support for VTI, do you see this happening any soon?
We use VTI for connecting to some public clouds and with the volume of traffic there is no need to purchase a router to do this job and would create some issues if we would swap from ASA (where is supported) to FTD, we could just lose in one shot BGP dynamic routing since there is no VTI support (yet).
Thanks and again ,sorry for the OT
6.6 will be out this week I believe and it doesn’t support VTI that I heard. The big new feature for 6.6. is VRF… I haven’t started 6.7 beta yet so I am not sure what that covers.
Hi Todd,
Thanks for your reply ealier.
I was looking for a comparison of CDO vs FMC but I haven’t found any hit and miss list that could help me.
“If” you have some time could you dedicate an entry for this? I would like to understand what we miss if we go CDO and if it works really better with FTD compared to FMC.
Also there is the price difference, it seems to me that CDO is way cheaper rather than FMC for an amount of nodes up to 100.
Thanks in advance!
First, Giovanni, I do like CDO, but it’s still in beta mostly for Firepower, and wiht that said, I’d stay iwth the FMC for now as it has a lot more features. CDO is only cheaper at first, then gets expensive as you add devices. For example, if you have 10 ASA’s it would be $10,000 a year for the license, however, all your switches are no cost for the license.
I would wait a little on the CDO, but I still think CDO is the future.
Giovanni, 6.7 code will support VTI finally. Should be out towards end of year
Had a physical FMC 1000 device fail upgrading to 6.5.0.4. It turns out it was a flash issue in the hardware. The FMC upgraded fine to 6.5.0.0. It was running okay but then would not install the patch to 6.5.0.4. It kept failing. Cisco TAC had to RMA the unit. Not cool.
The error you will see during patch install is – Fatal error: error running script 000_start/112_CF_check.sh
Jonathan I am sorry you went through that.
Seen that error myself
Tell them you want a 1600 cause the 1000 have been EOL for a while
This might be a blessing! Let me know
It was part of an H/A pair so they had to send another 1000.
On a different note, is there a way to bypass the IPS for certain IP ranges easily? For instance, all our outside > in to DMZ rules have IPS on them and we want certain IP ranges not to be scanned by the IPS, but I don’t want to create a rule for every DMZ rule to allow these ranges with no IPS scanning.
aah..too bad on the 1k
yes, you can FastPath any layers 3 or 4 in the PreFilter, which bypasses snort